Pop Quiz: Disaster strikes. Access to your network and your data is gone. Business comes to a standstill. What do you do?
Disasters come in many forms, but let’s say this disaster is a Ransomware attack – a scenario much more common than fires, earthquakes floods or other types of catastrophes.
A well-meaning but untrained employee opens an email from what seems to be a trusted source. It could be an entity like FedEx or perhaps one of your business contacts. Cyber criminals hack an end user somewhere and then send phishing emails in the victim’s name to everyone in their address book. They also ‘spoof’ or copy the email setups and logos of big companies and even Federal Institutions like the IRS, so the phishing FedEx email looks legit. It provides a link to track a package someone sent to your company. But it is not legitimate, and as soon as your employee clicks on the link, their computer freezes, and a screen appears that looks something like this:
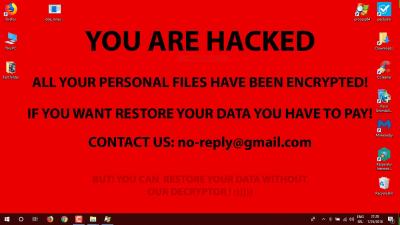
This is only the beginning. The Ransomware is already inside and finding its path to the rest of your network. The employee should be trained to immediately turn off the computer. By now, going to the Start Menu for a standard shutdown is unavailable. The only way is by holding in the power button until the device shuts down - or even unplugging it. The quicker the action, the easier the cleanup. The tide of the virus must be stemmed immediately.
That is the very first step. Now what? Call IT support, whether an in-house department or a 3rd party IT consulting service. One of the benefits of using a top-notch Managed IT Services firm like ITFirm.com, is that with their proactive monitoring, their Help Desk technicians should already be getting alarms that your system has been breached.
ITFirm.com configures our clients’ Cybersecurity to easily isolate and trap the malware in the initially infected device to prevent spread. Any reputable and experienced IT provider should have these policies and procedures in place.
This is only what needs to happen within a minute or two after the attack, but it is only a small but crucial first step in a comprehensive Backup and Disaster Recovery Plan. This is the point where the plan is implemented. The IT services team, in conjunction with your company’s management, will now do the heavy lifting to restore normalcy to your network operations.
How do you write a good disaster recovery plan?
Just as with any enterprise, the old saying “If you fail to plan, you plan to fail” is of paramount importance when it comes to a Backup and Disaster Recovery Plan. Putting an effective plan together requires a thorough process with pinpoint attention to detail.
The basic steps required to implement an all-inclusive and reliable plan:
1) Top Management Commitment
Your IT team does not exist in a vacuum and does not presume to act without prior management approval. Everyone must be on board with The Plan. The IT crew will do the behind-the-scenes work, but it is company management that must approve and coordinate the plan with the employees, so their involvement and commitment to the plan is absolute necessity.
2) Select and Organize a Planning Committee
IT, management, all department heads, and all areas of the company that would be affected by the disaster must be represented. The committee will define and delegate duties and determine the scope of the plan and set the standards for the activities listed below.
3) Risk Assessment
Assess and analyze the potential dangers to all areas of the organization for impacts and consequences of each disaster scenario. For example, a fire will present different consequences than a Ransomware attack – such as an orderly evacuation plan. Risks and the costs involved in responding to and minimizing the exposure because of the various possible disasters need also be analyzed.
4) Establishment of Priorities
The importance or ’pecking order’ of all areas of Processing and Operations. Putting ‘first-things-first.’ Typically, data and communications should come first because they allow other areas of the organization to continue. For example, in manufacturing, the shipping department should be down in the pecking order because they will have nothing to ship if nothing is being manufactured.
5) Set Recovery Strategies and Tactics
For each department, determine the steps to be taken and who will take command of ensuring those steps are performed. The objective, much as for those in ‘Establish Priorities’ above, is to enable the continuity of business as the disaster is being addressed. Establishing what is to be done and by which key personnel prevents any possible confusion.
6) Write Out the Plan
Starting with the outline, the final plan needs to be in a standardized format and must adhere to every minute detail in understandable, non-ambiguous wording. The idea that any part of the plan could be open to ‘interpretation’ must be avoided – these must be clear-cut directives. All functions of all departments must be clearly assigned. A haphazardly written plan is as bad as no plan at all.
7) Establish Criteria for Testing
Testing, analysis, and ‘tweaking’ of the plan will be an ongoing process. Develop dependable testing procedures that allow you to foresee any weak spots and make appropriate adjustments. Any surprises on the day of an actual disaster are a disaster of their own.
8) Testing
Perform the first test based only on the plan and the testing criteria and update the plan as needed. A plan is rarely ‘bulletproof’ the first time out.
10) Final Plan Approval
Following a series of tests and adjustments, and all contingencies are well covered, set the plan in stone – for now – future adjustments may be necessary. Ongoing testing should be scheduled at regular, agreed-upon intervals. The world changes, as does technology, so follow-up tests may show inadequacies that were not present when the final plan was approved.
Cloudian offers a comprehensive guide to putting together a good Backup & Disaster Recovery Plan HERE.
Frequently Asked Questions
Q: What is the difference between having good backups and having a good disaster recovery plan?
A: In the case of a Ransomware attack – or any disaster that destroys your network and servers, no backups = no recovery. Without reliable and tested offsite data backups in place, there really is no recovery from a disaster, at least from an IT services point of view.
Once the data is gone and exists nowhere else, a typical business will not survive – over 60% of businesses that lose their data fold within a year – usually within months. You need both the backups and the plan. If you have some sort of IT services, but do not have either backups or a disaster recovery plan in place, perhaps it’s time to re-evaluate the quality of your IT support.
Q: What are the different types of data backup locations?
A: Local Backup – usually not connected to the main network – the fastest way to restore data.
Cloud Backup – off premises. This is slower, but your data should be made safe in the cloud.
Cloud to Cloud Backup – an extra measure of protection.
Q: What is the best method for data recovery?
A: Depending on the nature of the disaster, the fastest way to restore data is from your local backups, which may not be available in the event of a fire, flood or earthquake – at that point, rely on cloud backups, which are slower, but offsite.
Q: What is incident response plan?
A: The Incident Response Plan (IRP) is a part of the overall Backup & Disaster Recovery Plan, but it only deals with the IT support factors and procedures following an attack or data breach. With minor incidents, like an employee forwarding aa suspicious email to the IT services team, the IRP may be the only section of the larger plan that needs to be implemented.
How secure is your network?
As a longstanding, reputable member of the Charlotte IT Support community, ITFirm.com offers a FREE, no-risk network and Cybersecurity assessment. We perform a non-intrusive scan that allows us to deliver a comprehensive report of the state of your system and its vulnerabilities that is yours to keep. There are no strings attached, and you are under no obligation to ever use our Managed IT Services.
The two best defenses are next-generation Cybersecurity to protect your data from theft, and a top-notch Managed Services Provider to ensure continued reliability and defenses against newly emerging threats.
We put our 100% Money Back Guarantee in writing, so there is no risk in trying us out. Because we do not require a ‘hard’ contract, our clients can fire us at any time with 30 days’ notice. We have to be good.
Among the Managed IT Services we provide:
IT HelpDesk Service
Onsite IT Support
Cybersecurity
Cloud migration and management
Email migration services
Backup and disaster recovery
VoIP phone systems
IT disposition and recycling
Office moves
White label services (IT to IT)
For more information, or to receive your FREE no-risk network and security assessment, just fill out the form on this page or call us at:
704-565-9705

